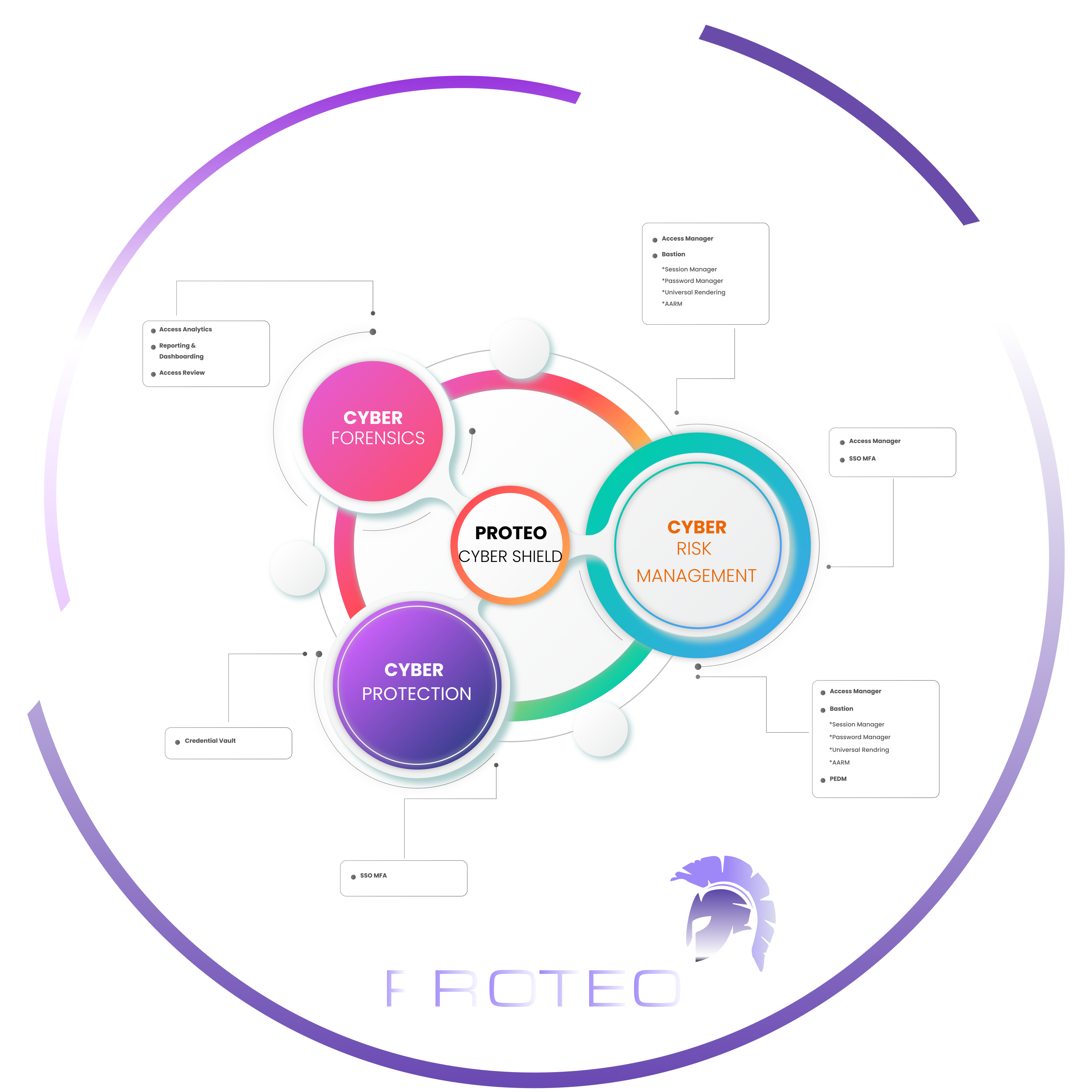
Project
Full CyberResilience Audit
Im Rahmen eines umfassenden CyberSecurity-Audits begleiteten wir einen europaweit tätigen Onlinebroker bei der Weiterentwicklung seiner IT-Sicherheitsarchitektur im Kontext der neuen DORA-Verordnung (Digital Operational Resilience Act). Ausgangspunkt war die Fragestellung, inwieweit bestehende Strukturen den steigenden Anforderungen an operative Resilienz, Angriffserkennung und regulatorische Nachweisfähigkeit bereits genügen.
Gemeinsam mit den relevanten Fach- und IT-Einheiten wurde der Status quo der technischen und organisatorischen Sicherheitsmaßnahmen systematisch analysiert. Identifizierte Schwachstellen wurden risikobasiert priorisiert und in einen umsetzungsnahen Maßnahmenkatalog überführt, der nahtlos in bestehende Prozesse integriert werden konnte. Ein besonderer Schwerpunkt lag auf der Härtung kritischer Systeme sowie dem Aufbau eines konsistenten Governance- und Steuerungsrahmens zur nachhaltigen Verankerung der DORA-Anforderungen.
-
DORA-Gap-Analyse inklusive Umsetzungs-Roadmap
-
Bewertung und Härtung der bestehenden IT-Architektur
-
Aufbau eines dynamischen, risikobasierten Cyber-Risikomanagements
-
Integration von Audit- und Prüfungsfeststellungen in das bestehende ISMS
Project
Forensische Analyse nach Cyberangriff: Angriffspfadanalyse & Prävention für einen Krypto-Handelsplatz
Nach einem gezielten Cyberangriff auf einen Handelsplatz für Digitalwährungen wurden große Mengen an Kryptowährungen aus Kunden-Wallets entwendet. Unsere Aufgabe bestand darin, die Angriffsmuster forensisch zu analysieren, die technischen Schwachstellen zu identifizieren und nachvollziehbar darzustellen, wie sich der Angreifer durch die Systemlandschaft bewegt hatte.
Neben der Aufklärung der Tat lag der Fokus auf der Entwicklung eines Maßnahmenplans zur Behebung der Sicherheitslücken und zur nachhaltigen Erhöhung der Cyberresilienz. In enger Abstimmung mit IT, Compliance und Management wurde ein zukunftssicheres Sicherheitskonzept etabliert, das sowohl technische Schutzmechanismen als auch organisatorische Notfallprozesse umfasst.
-
Forensische Untersuchung des Angriffsvektors
-
Schwachstellenanalyse und technische Ursachenforschung
-
Entwicklung eines mehrstufigen Sicherheitskonzepts
-
Einführung eines Frühwarnsystems für Wallet-bezogene Anomalien
Project
Forensischer Taskforce-Einsatz nach Token-Diebstahl aus einem Crypto-Wallet
Im Rahmen eines behördlich initiierten Taskforce-Einsatzes wurden wir nach dem Abfluss digitaler Vermögenswerte aus einem Crypto-Wallet hinzugezogen. Ziel des Projekts war es, den technischen und organisatorischen Entstehungsweg des Vorfalls nachvollziehbar zu rekonstruieren und belastbare Erkenntnisse zur Ursache des Token-Verlusts zu gewinnen. Aufgrund der laufenden Ermittlungen galt während des gesamten Projekts höchste Vertraulichkeit.
Im Zentrum der Untersuchung stand die forensische Analyse der zugrunde liegenden Systemlandschaft, der Zugriffspfade sowie relevanter Log- und Transaktionsdaten. Die Analyse erfolgte ergebnisoffen und ohne Vorannahmen hinsichtlich eines technischen Exploits. Im Verlauf der Untersuchungen verdichteten sich die Hinweise, dass der Zugriff nicht durch eine Schwachstelle in der Wallet- oder Blockchain-Infrastruktur selbst erfolgte, sondern durch gezielte Social-Engineering-Maßnahmen, die zur Kompromittierung von Zugangs- und Administrationsrechten führten. Die Untersuchungsergebnisse wurden strukturiert aufbereitet und den zuständigen Ermittlungsbehörden zur weiteren Verwendung übergeben.
-
Forensische Analyse eines Token-Abflusses aus einem Crypto-Wallet
-
Rekonstruktion von Zugriffs- und Transaktionspfaden
-
Auswertung von System-, Zugriffs- und Ereignisprotokollen
-
Identifikation von Social-Engineering-basierten Angriffsmustern
Project
Technische Code-Forensik im Rahmen einer M&A-Transaktion mit hohem Technologieanteil
Im Rahmen eines komplexen M&A-Projekts mit starkem Technologie- und Softwarefokus wurden wir von einer federführenden Wirtschaftskanzlei hinzugezogen, um die technische Substanz des Zielunternehmens unabhängig zu bewerten. Für externe Parteien stellte die zugrunde liegende Softwareplattform eine weitgehend geschlossene Blackbox dar, deren Qualität, Integrität und rechtliche Unbedenklichkeit auf Basis klassischer Due-Diligence-Ansätze nur eingeschränkt beurteilt werden konnte.
Aufgabe war es, durch gezielte forensische Untersuchungen auf Code- und Architekturebene festzustellen, ob die Software frei von urheberrechtlichen Risiken ist, keine sicherheitskritischen Einfallstore für Schadsoftware enthält und insgesamt einem zeitgemäßen, belastbaren Architekturverständnis entspricht. Die Analyse erfolgte unabhängig und ergebnisoffen. In zwei der drei untersuchten Dimensionen wurden erhebliche Defizite identifiziert, die eine unmittelbare Transaktionsfreigabe ausschlossen. Erst nach der vollständigen Behebung der festgestellten Mängel und einer erneuten technischen Validierung konnte das Projekt erfolgreich zum Abschluss gebracht werden.
-
Forensische Code- und Architekturprüfung im M&A-Kontext
-
Analyse möglicher Urheberrechts- und Lizenzverletzungen
-
Identifikation sicherheitskritischer Schwachstellen auf Code-Eben
-
Bewertung der Software-Architektur im Hinblick auf Skalierbarkeit und Wartbarkeit
Project
Integrierte Security- & Trust-Management-Plattform zur automatisierten Compliance-Steuerung
Ausgangspunkt für die Entwicklung der eigenen Security- und Trust-Management-Plattform war die zunehmende Komplexität regulatorischer Anforderungen sowie die Erkenntnis, dass klassische Compliance-Ansätze den dynamischen Anforderungen moderner IT- und Geschäftsmodelle nicht mehr gerecht werden. Ziel war es, eine zentrale Plattform zu schaffen, die Sicherheits-, Governance- und Compliance-Anforderungen nicht isoliert dokumentiert, sondern ganzheitlich, kontinuierlich und automatisiert steuert.
Die entwickelte Plattform automatisiert die Anforderungen einer Vielzahl international anerkannter Security- und Compliance-Frameworks. Sie konsolidiert technische, organisatorische und prozessuale Nachweise, bewertet den aktuellen Reifegrad in Echtzeit und macht Abweichungen sowie Handlungsbedarfe transparent. Durch den hohen Automatisierungsgrad werden manuelle Aufwände drastisch reduziert, Prüfungsprozesse signifikant beschleunigt und Compliance als fortlaufender, steuerbarer Zustand etabliert. Die Plattform ist vollständig eigenentwickelt, modular aufgebaut und für den Einsatz in hochregulierten Umfeldern ausgelegt.
-
Automatisierung internationaler Security- und Compliance-Frameworks
-
Kontinuierliche Ermittlung und Fortschreibung des Sicherheits- und Compliance-Reifegrads
-
Zentrale Konsolidierung technischer, organisatorischer und prozessualer Nachweise
-
Echtzeit-Transparenz über Abweichungen, Risiken und Maßnahmen
Project
Cyber Due Diligence & CyberRisk-Analyse zur Vorbereitung externer IT-Prüfungen
Im Vorfeld einer angekündigten externen IT-Prüfung durch eine Aufsichts- bzw. Kontrollbehörde beauftragte uns ein reguliertes Unternehmen mit der Durchführung einer umfassenden Cyber Due Diligence. Ziel war es, bestehende Strukturen, Prozesse und Sicherheitsmaßnahmen frühzeitig auf ihre regulatorische, organisatorische und technische Angemessenheit zu überprüfen und identifizierte Schwachstellen vor dem eigentlichen Audit strukturiert zu adressieren.
Im Rahmen des Projekts wurden sowohl die bestehende IT- und Sicherheitslandschaft als auch relevante Geschäfts- und Steuerungsprozesse ganzheitlich analysiert. Neben der Bewertung technischer Schutzmaßnahmen lag ein besonderer Fokus auf der formalen Ausgestaltung von Verfahren, Rollenmodellen und Berechtigungssystemen. Die Ergebnisse wurden in eine konsistente CyberRisk-Bewertung überführt und dienten als Grundlage für die Ableitung einer integrierten CyberSecurity-, Datensicherheits- und DORA-Strategie, die sowohl operative Umsetzbarkeit als auch regulatorische Nachweisfähigkeit sicherstellt.
-
Durchführung einer Cyber Due Diligence als prüfungsvorbereitende Maßnahme
-
Bestands- und Prozessanalysen entlang IT, Security und Governanc
-
Dokumentation von Verfahren, Rollen, Verantwortlichkeiten und Kontrollmechanismen
-
Analyse von Berechtigungskonzepten und Unvereinbarkeiten
Project
Incident-, Melde- und Governance-Strukturen für einen regulierten Finanzdienstleister
Ausgangspunkt dieses Projekts war die zunehmende öffentliche und regulatorische Aufmerksamkeit auf unzureichend strukturierte Incident-Prozesse sowie verspätete oder inkonsistente Meldungen sicherheitsrelevanter Vorfälle. Ein europaweit tätiger Finanzdienstleister trat mit dem Anliegen an uns heran, bestehende Incident- und Meldeverfahren ganzheitlich zu überprüfen und so auszurichten, dass sowohl operative Handlungsfähigkeit als auch regulatorische Nachweisbarkeit jederzeit gewährleistet sind.
Im Projektverlauf wurden die bestehenden Prozesse zur Erkennung, Klassifikation, Eskalation und Meldung von Sicherheitsvorfällen entlang des gesamten Lebenszyklus analysiert. Besonderes Augenmerk lag auf der klaren Abgrenzung von Verantwortlichkeiten, der Entscheidungslogik bei meldepflichtigen Vorfällen sowie der Verzahnung technischer Ereignisse mit organisatorischen und rechtlichen Bewertungsschritten. Gemeinsam mit IT, GRC, Legal und Management wurde ein konsistenter Governance-Rahmen entwickelt, der operative Abläufe, regulatorische Anforderungen und Management-Entscheidungen nachvollziehbar miteinander verbindet.
-
Analyse und Neustrukturierung der Incident-Lifecycle-Prozesse
-
Definition klarer Rollen, Zuständigkeiten und Eskalationsstufen
-
Entwicklung einer konsistenten Melde- und Klassifizierungslogik
-
Abbildung regulatorischer Anforderungen in operativen Entscheidungsprozessen
Project
API- & Plattform-Security für eine datengetriebene Finanz- und Serviceplattform
Vor dem Hintergrund öffentlich bekannt gewordener Datenlecks und Missbrauchsfälle über unzureichend abgesicherte Programmierschnittstellen wandte sich der Betreiber einer europaweit genutzten digitalen Plattform an uns, um die Sicherheit seiner API-basierten Systemlandschaft grundlegend zu überprüfen. Ziel war es, die wachsende Abhängigkeit von APIs nicht als Risikofaktor, sondern als kontrollierbaren Bestandteil der Gesamtarchitektur zu etablieren.
Im Rahmen des Projekts wurden sämtliche produktiven und internen Schnittstellen systematisch erfasst und entlang typischer Angriffsszenarien analysiert. Der Fokus lag dabei weniger auf klassischen Schwachstellen, sondern auf logischen Zugriffspfaden, Berechtigungsmodellen und Missbrauchsmöglichkeiten innerhalb komplexer Plattformprozesse. Gemeinsam mit Entwicklung, Betrieb und Architektur wurden identifizierte Risiken priorisiert und in ein konsistentes Sicherheits- und Governance-Konzept überführt, das sich in bestehende Entwicklungs- und Betriebsprozesse integrieren ließ.
-
Vollständige Erfassung und Klassifizierung aller APIs
-
Analyse von Authentifizierungs-, Autorisierungs- und Token-Mechanismen
-
Prüfung der API-Logik auf Missbrauchs- und Eskalationsszenarien
-
Umsetzung eines durchgängigen API-Governance- und Kontrollrahmens
Project
Ransomware-Resilienz & Incident-Readiness für ein KRITIS-nahes Infrastrukturunternehmen
Nach mehreren öffentlich bekannt gewordenen Ransomware-Vorfällen in kritischen Infrastrukturen trat ein bundesweit tätiges Infrastrukturunternehmen mit dem Ziel an uns heran, die eigene Widerstandsfähigkeit gegenüber gezielten Cyberangriffen strukturiert zu überprüfen und zu stärken. Im Fokus stand dabei nicht allein die Prävention, sondern insbesondere die Fähigkeit, sicherheitsrelevante Vorfälle frühzeitig zu erkennen, wirksam zu begrenzen und regulatorisch korrekt zu behandeln.
Im Rahmen des Projekts wurde die bestehende IT- und Sicherheitsarchitektur ganzheitlich analysiert – von der Netzsegmentierung über Zugriffs- und Berechtigungskonzepte bis hin zu Backup- und Wiederanlaufverfahren. Gemeinsam mit IT, Betrieb und Management wurden realistische Angriffsszenarien abgeleitet, bestehende Schutzmechanismen bewertet und ein priorisierter Maßnahmenkatalog entwickelt. Ein besonderer Schwerpunkt lag auf der Verzahnung technischer Schutzmaßnahmen mit klar definierten Entscheidungs-, Eskalations- und Kommunikationswegen im Ernstfall.
-
Ransomware-Readiness-Assessment auf Basis realer Angriffsszenarien
-
Analyse und Härtung kritischer System- und Netzwerksegmente
-
Bewertung und Neuausrichtung von Backup- und Recovery-Strategien
-
Konzeption eines strukturierten Incident-Response-Frameworks
Project
Präventives Social-Engineering- & Awareness-Programm für eine wissensintensive Organisation
Nach mehreren öffentlich bekannt gewordenen Vorfällen, bei denen Angriffe nicht über technische Schwachstellen, sondern über gezielte Manipulation von Mitarbeitenden erfolgten, entschied sich eine wissensintensive Organisation für einen präventiven Ansatz. Ziel war es, Social Engineering nicht isoliert als Schulungsthema zu behandeln, sondern als reales Cyberrisiko systematisch in Sicherheitsarchitektur, Prozesse und Unternehmenskultur zu integrieren.
Im Rahmen des Projekts wurden typische Angriffsvektoren analysiert, reale Angriffsszenarien modelliert und organisationsspezifische Risikoprofile erstellt. Darauf aufbauend wurde ein mehrstufiges Awareness- und Präventionskonzept entwickelt, das technische, organisatorische und menschliche Faktoren miteinander verknüpft. Besonderes Augenmerk lag darauf, Sicherheitsbewusstsein nicht durch einmalige Trainings, sondern durch kontinuierliche Sensibilisierung, messbare Lernfortschritte und klare Eskalationsmechanismen nachhaltig zu verankern.
-
Analyse organisationsspezifischer Social-Engineering-Risikoprofile
-
Entwicklung realistischer Angriffsszenarien (Phishing, Pretexting, Impersonation)
-
Durchführung gezielter Awareness- und Simulationstrainings
-
Definition klarer Melde- und Eskalationswege bei Verdachtsfällen
Project
Secure Phone – autarke, abhörsichere Kommunikationslösung für hochsensible Einsatzbereiche
Ausgangspunkt für die Entwicklung des Secure Phone war ein Mandat aus einem besonders sensiblen Bereich der Wirtschaft, bei dem der Schutz strategischer Unternehmenswerte oberste Priorität hatte. Ziel war es, ungewollte Informationsabflüsse nicht nur reaktiv zu erkennen, sondern proaktiv zu verhindern – insbesondere in Szenarien, in denen gezielte Infiltration, technische Überwachung oder Abhörmaßnahmen nicht ausgeschlossen werden konnten.
Auf Basis dieser Anforderungen wurde eine vollständig eigenständige Kommunikationslösung konzipiert, die sowohl auf Hardware- als auch auf Softwareebene höchste Sicherheitsanforderungen erfüllt. Die entwickelte Hardware ist vollständig autark, verzichtet auf externe Abhängigkeiten und wurde so ausgelegt, dass potenzielle Angriffs- und Abhörpunkte systematisch ausgeschlossen werden. Ergänzend wurde eine speziell angepasste Systemarchitektur implementiert, die sichere Kommunikation auch in besonders exponierten Umgebungen ermöglicht.
-
Entwicklung einer vollständig autarken, abhörsicheren Kommunikationshardware
-
Schutz vor gezielten Abhör-, Infiltrations- und Manipulationsversuchen
-
Reduktion externer Abhängigkeiten auf Hardware- und Systemebene
-
Speziell gehärtete Kommunikations- und Betriebssystemarchitektur
Project
CyberRisk-Dashboard mit Echtzeitbewertung und Management-Fokus
Ausgangspunkt für die Entwicklung des CyberRisk-Dashboards war die wiederkehrende Beobachtung, dass Cyberrisiken zwar technisch detailliert erfasst werden, ihre Bedeutung für Management-Entscheidungen jedoch häufig fragmentiert oder zeitverzögert sichtbar wird. Ziel war es daher, eine zentrale Plattform zu schaffen, die sicherheitsrelevante Informationen aus unterschiedlichen Quellen konsolidiert, kontextualisiert und in eine fortlaufende, nachvollziehbare Risikobewertung überführt.
Das Dashboard wurde als modular aufgebaute Eigenentwicklung konzipiert, die technische Ereignisse, organisatorische Faktoren und regulatorische Anforderungen miteinander verknüpft. In Echtzeit werden relevante Signale aggregiert, priorisiert und entlang definierter Risikokategorien bewertet. Besonderer Wert wurde darauf gelegt, technische Detailtiefe und Management-Tauglichkeit klar zu trennen: Während operative Einheiten tiefgehende Analysen durchführen können, erhalten Entscheider eine verdichtete, belastbare Sicht auf die aktuelle CyberRisk-Lage und deren Entwicklung über die Zeit.
-
Zentrale Aggregation technischer, organisatorischer und regulatorischer Risikosignale
-
Echtzeitbasierte Bewertung und Priorisierung von Cyberrisiken
-
Trennung operativer Detailansichten und Management-Dashboards
-
Abbildung von Risikotrends, Eskalationsstufen und Maßnahmenstatus
Project
Automatisierte DORA-Readiness-Logik zur kontinuierlichen Resilienzbewertung
Ausgangspunkt für die Entwicklung der automatisierten DORA-Readiness-Logik war die Erkenntnis, dass regulatorische Anforderungen zur digitalen operationalen Resilienz häufig punktuell bewertet werden, während ihr tatsächlicher Erfüllungsgrad im laufenden Betrieb nur eingeschränkt sichtbar ist. Ziel war es daher, eine Logik zu entwickeln, die den DORA-Reifegrad nicht statisch dokumentiert, sondern kontinuierlich, nachvollziehbar und prüfungstauglich abbildet.
Die entwickelte Lösung übersetzt die Anforderungen der DORA-Verordnung in strukturierte Prüfkriterien, Steuerungsparameter und messbare Indikatoren. Technische, organisatorische und prozessuale Informationen werden automatisiert zusammengeführt, bewertet und in einen konsistenten Reifegrad überführt. Abweichungen, Handlungsbedarfe und Fortschritte werden transparent dargestellt und können sowohl operativ als auch auf Management-Ebene nachvollzogen werden. Die Logik ist modular aufgebaut und lässt sich in bestehende Governance-, Risiko- und Kontrollsysteme integrieren.
-
Übersetzung regulatorischer DORA-Anforderungen in prüfbare Steuerungskriterien
-
Automatisierte Ermittlung und Fortschreibung des DORA-Reifegrads
-
Verknüpfung technischer, organisatorischer und prozessualer Informationen
-
Transparente Darstellung von Abweichungen, Maßnahmen und Fortschritten
Project
Audit-Trail- und Evidence-Repository zur prüfungssicheren Nachweisführung
Ausgangspunkt für die Entwicklung des Audit-Trail- und Evidence-Repositories war die wiederkehrende Erfahrung, dass sicherheitsrelevante Nachweise zwar inhaltlich vorhanden sind, jedoch über unterschiedliche Systeme, Verantwortlichkeiten und Formate verteilt vorliegen. Dies erschwert nicht nur interne Steuerung, sondern insbesondere die strukturierte Vorbereitung und Durchführung externer Prüfungen.
Die entwickelte Lösung dient als zentrale, revisionssichere Ablage für alle prüfungsrelevanten Informationen im Kontext von CyberSecurity, IT-Governance und regulatorischen Anforderungen. Ereignisse, Maßnahmen, Entscheidungen und technische Nachweise werden automatisch oder manuell erfasst, versioniert und in einen nachvollziehbaren zeitlichen Zusammenhang gestellt. Der vollständige Audit-Trail ermöglicht es, sowohl operative Entwicklungen als auch Management-Entscheidungen konsistent und belastbar nachzuweisen.
-
Zentrale, strukturierte Ablage prüfungsrelevanter Nachweise
-
Lückenlose Dokumentation von Maßnahmen, Entscheidungen und Ereignissen
-
Versionierung und zeitliche Nachvollziehbarkeit aller Artefakte
-
Unterstützung interner und externer Prüfungen durch konsistente Evidenzen
Project
Automatisiertes Security-Assessment-Tool für weit verbreitete CMS-Plattformen mit Zertifizierungsansatz
Ausgangspunkt für die Entwicklung dieses Tools war die Beobachtung, dass eine große Anzahl öffentlich erreichbarer Websysteme auf verbreiteten Content-Management-Systemen basiert und häufig unzureichend gewartet oder abgesichert ist. Diese Systeme stellen ein attraktives Ziel für automatisierte Angriffe dar und dienen nicht selten als Einfallstor für weitergehende Kompromittierungen. Ziel war es, ein skalierbares Prüfverfahren zu schaffen, das Sicherheitsrisiken frühzeitig erkennt und Administratoren konkret bei der Behebung unterstützt.
Die entwickelte Lösung analysiert CMS-Installationen automatisiert auf bekannte und kontextbezogene Sicherheitsprobleme. Neben der Identifikation technischer Schwachstellen werden konkrete, umsetzbare Handlungsempfehlungen bereitgestellt, die sich an der jeweiligen Systemkonfiguration orientieren. In Kombination mit einem nachgelagerten, strukturierten Security-Audit kann der Sicherheitszustand des Systems abschließend validiert und in Form einer Zertifizierung dokumentiert werden. Damit wird aus einer rein technischen Prüfung ein nachvollziehbarer, prüfungsfähiger Sicherheitsnachweis.
-
Automatisierte Sicherheitsanalyse weit verbreiteter CMS-Systeme
-
Identifikation technischer Schwachstellen und Fehlkonfigurationen
-
Ableitung konkreter, administrativ umsetzbarer Handlungsempfehlungen
-
Skalierbarer Einsatz auch bei großen Systemlandschaften
Project
Forensische Beseitigung eines Hardware-Locks im Rahmen behördlicher Ermittlungen
Im Zuge laufender Ermittlungen wurden wir von behördlicher Seite hinzugezogen, um die technische Analyse und Beseitigung eines hardwareseitigen Zugriffsschutzes zu unterstützen. Der betroffene Gerätetyp war durch einen proprietären Hardware-Lock gesichert, der den Zugriff auf gespeicherte Daten sowie die weitere technische Analyse verhinderte. Ziel des Einsatzes war es, den Sperrmechanismus kontrolliert aufzuheben, ohne die Integrität potenziell beweisrelevanter Informationen zu beeinträchtigen.
Die Untersuchung erfolgte unter streng kontrollierten Rahmenbedingungen und in enger Abstimmung mit den zuständigen Stellen. Im Fokus standen die Analyse der zugrunde liegenden Hardware-Architektur, die Identifikation des Sperrmechanismus sowie die Entwicklung eines zielgerichteten Vorgehens zur Umgehung des Locks. Der Zugriff wurde ausschließlich zu forensischen Zwecken hergestellt, sämtliche Schritte dokumentiert und die Ergebnisse in verwertbarer Form zur Verfügung gestellt.
-
Forensische Analyse hardwarebasierter Zugriffssperren
-
Untersuchung proprietärer Lock- und Schutzmechanismen
-
Kontrollierte Aufhebung von Hardware-Locks unter Beweiswahrung
-
Tiefgehende Analyse von Hardware-Architektur und Speicherzugriffen
Project
Red-Teaming-Einsatz zur realitätsnahen Überprüfung der Cyber-Resilienz
Im Rahmen eines strategischen Sicherheitsprogramms beauftragte uns ein größeres Unternehmen mit der Durchführung eines Red-Teaming-Einsatzes, um die tatsächliche Widerstandsfähigkeit seiner technischen und organisatorischen Schutzmaßnahmen unter realistischen Angriffsbedingungen zu überprüfen. Ziel war es nicht, einzelne Schwachstellen isoliert zu identifizieren, sondern das Zusammenspiel aus Technik, Prozessen und menschlichem Verhalten ganzheitlich zu testen.
Der Einsatz erfolgte auf Basis definierter Zielbilder und klarer Rahmenbedingungen. Unter Nutzung realitätsnaher Angriffsvektoren wurde versucht, unautorisierte Zugriffe zu erlangen, Sicherheitsmechanismen zu umgehen und kritische Systeme zu kompromittieren. Dabei kamen sowohl technische als auch soziale Angriffsmethoden zum Einsatz. Die Ergebnisse wurden nicht als reine Befundliste dokumentiert, sondern in konkrete Risikoszenarien überführt und gemeinsam mit den verantwortlichen Stellen in priorisierte Maßnahmen übersetzt.
-
Planung und Durchführung eines kontrollierten Red-Teaming-Einsatzes
-
Simulation realer Angriffs- und Eskalationspfade
-
Kombination technischer Angriffe und Social-Engineering-Methoden
-
Bewertung der Erkennungs-, Reaktions- und Eskalationsfähigkeit
Project
C-Level-Red-Teaming zur Überprüfung von Entscheidungs- und Krisenfähigkeit
Im Rahmen eines unternehmensweiten Sicherheitsprogramms wurde ein C-Level-Red-Teaming initiiert, um nicht primär technische Schutzmaßnahmen, sondern die Entscheidungs-, Eskalations- und Steuerungsfähigkeit auf oberster Führungsebene unter realistischen Angriffsbedingungen zu überprüfen. Ausgangspunkt war die Erkenntnis, dass Cybervorfälle weniger an fehlender Technik scheitern, sondern an unklaren Zuständigkeiten, verzögerten Entscheidungen oder widersprüchlicher Kommunikation auf Management-Ebene.
Der Red-Teaming-Einsatz kombinierte realitätsnahe technische Angriffsszenarien mit gezielten Stress- und Entscheidungssituationen für das Top-Management. Sicherheitsrelevante Ereignisse wurden schrittweise eskaliert, Entscheidungsoptionen bewusst verknappt und externe Rahmenbedingungen simuliert. Ziel war es, Transparenz darüber zu gewinnen, wie effektiv Führungsgremien unter Zeitdruck agieren, Informationen bewerten, Verantwortung übernehmen und steuernd eingreifen. Die Ergebnisse wurden strukturiert ausgewertet und in konkrete Governance-, Rollen- und Prozessanpassungen überführt.
-
Konzeption und Durchführung eines C-Level-fokussierten Red-Teaming-Szenarios
-
Simulation kritischer Entscheidungs- und Eskalationssituationen
-
Bewertung von Rollenverständnis, Verantwortlichkeiten und Entscheidungslogiken
-
Analyse von Kommunikations- und Abstimmungsprozessen im Krisenfall
Project
Gezielte Gegenmaßnahmen und Rückverfolgung bei laufendem Datenabfluss
In einem wirtschaftlich tätigen Unternehmen wurden wir auf Initiative des Informationssicherheitsbeauftragten hinzugezogen, nachdem ungewöhnliche Systemaktivitäten festgestellt worden waren. Erste Analysen deuteten auf eine fortgeschrittene Kompromittierung mehrerer Server hin, bei der es bereits zu unautorisierten Datenabflüssen gekommen war. Ziel des Einsatzes war es, den Umfang des Angriffs zu bestimmen, den Abfluss zu kontrollieren und belastbare Erkenntnisse über die Angreifer zu gewinnen.
Im weiteren Verlauf der Untersuchung wurde bewusst auf eine sofortige Abschaltung der betroffenen Systeme verzichtet. Stattdessen wurden kontrollierte Gegenmaßnahmen eingeleitet, um die Angreifer in dem Glauben zu lassen, weiterhin Zugriff auf vermeintlich sensible Informationen zu haben. Über gezielt platzierte technische Artefakte und eigens eingesetzte proprietäre Technologien konnten die Aktivitäten nachvollzogen, Kommunikationspfade analysiert und eine Rückverfolgung ermöglicht werden. Die gewonnenen Erkenntnisse führten letztlich zur Identifizierung der Angreifer und wurden den zuständigen Stellen in verwertbarer Form übergeben.
-
Forensische Analyse kompromittierter Server und laufender Datenabflüsse
-
Kontrollierte Fortführung des Angriffs zur Gewinnung belastbarer Erkenntnisse
-
Einsatz gezielter Täuschungs- und Gegenmaßnahmen
-
Nutzung proprietärer Technologien zur technischen Rückverfolgung
Project
Analyse und Aufklärung eines Advanced Persistent Threat (APT)
Im Zuge wiederkehrender, zunächst unauffälliger Sicherheitsereignisse wurden wir beauftragt, die Möglichkeit eines langfristig angelegten, gezielten Angriffs zu prüfen. Einzelne Indikatoren deuteten darauf hin, dass es sich nicht um einen opportunistischen Angriff handelte, sondern um eine systematische, verdeckte Kompromittierung mit klar definiertem Erkenntnis- und Zugriffsziel.
Die Analyse konzentrierte sich auf die Rekonstruktion des zeitlichen Angriffsverlaufs, die Identifikation persistenter Zugriffspunkte sowie die Korrelation technischer Spuren über mehrere Systeme hinweg. Besonderes Augenmerk lag auf der Trennung von legitimen und manipulierten Aktivitäten sowie auf der Erkennung von Tarnmechanismen, die eine frühzeitige Entdeckung verhindert hatten. Die gewonnenen Erkenntnisse ermöglichten eine belastbare Einordnung des Angriffscharakters, die gezielte Unterbrechung der Persistenz sowie die Ableitung nachhaltiger Schutz- und Härtungsmaßnahmen.
-
Analyse langfristiger, zielgerichteter Angriffsmuster (APT)
-
Rekonstruktion von Angriffsphasen und Persistenzmechanismen
-
Korrelation verteilter technischer Indikatoren über längere Zeiträume
-
Identifikation verdeckter Zugriffs- und Kontrollstrukturen
Project
Datenschutz-Forensik und Darknet-Analyse zur Aufklärung interner Datenabflüsse
Ein E-Commerce-Anbieter trat an uns heran, nachdem sich mehrere Kunden gemeldet hatten und den Verdacht äußerten, personenbezogene Adressdaten seien unrechtmäßig weitergegeben oder verkauft worden. Neben der akuten Sorge um mögliche Datenschutzverstöße stand insbesondere das Risiko eines erheblichen Reputationsschadens im Raum. Ziel des Projekts war es, die Vorwürfe sachlich zu prüfen, Transparenz zu schaffen und aktiv zur Aufklärung beizutragen.
Im Rahmen des Projekts wurde zunächst das bestehende Datenschutz- und Zugriffskonzept überprüft, einschließlich der technischen und organisatorischen Maßnahmen zum Schutz personenbezogener Daten. Parallel dazu erfolgte eine gezielte Analyse einschlägiger Darknet-Marktplätze und Kommunikationskanäle, um mögliche Hinweise auf einen Datenabfluss zu identifizieren. Die Untersuchung ergab, dass die Bedrohung nicht von außen, sondern aus dem Inneren der Organisation herausging: Ein Mitarbeiter hatte sich unrechtmäßig Zugriff auf Datenbanken verschafft und personenbezogene Daten exfiltriert. Die Erkenntnisse wurden strukturiert dokumentiert und zur weiteren Aufarbeitung bereitgestellt.
-
Überprüfung des Datenschutz- und Zugriffskonzepts
-
Analyse interner Berechtigungs- und Kontrollmechanismen
-
Gezielte Darknet-Recherche nach Hinweisen auf Datenabflüsse
-
Forensische Rekonstruktion interner Zugriffs- und Exfiltrationspfade