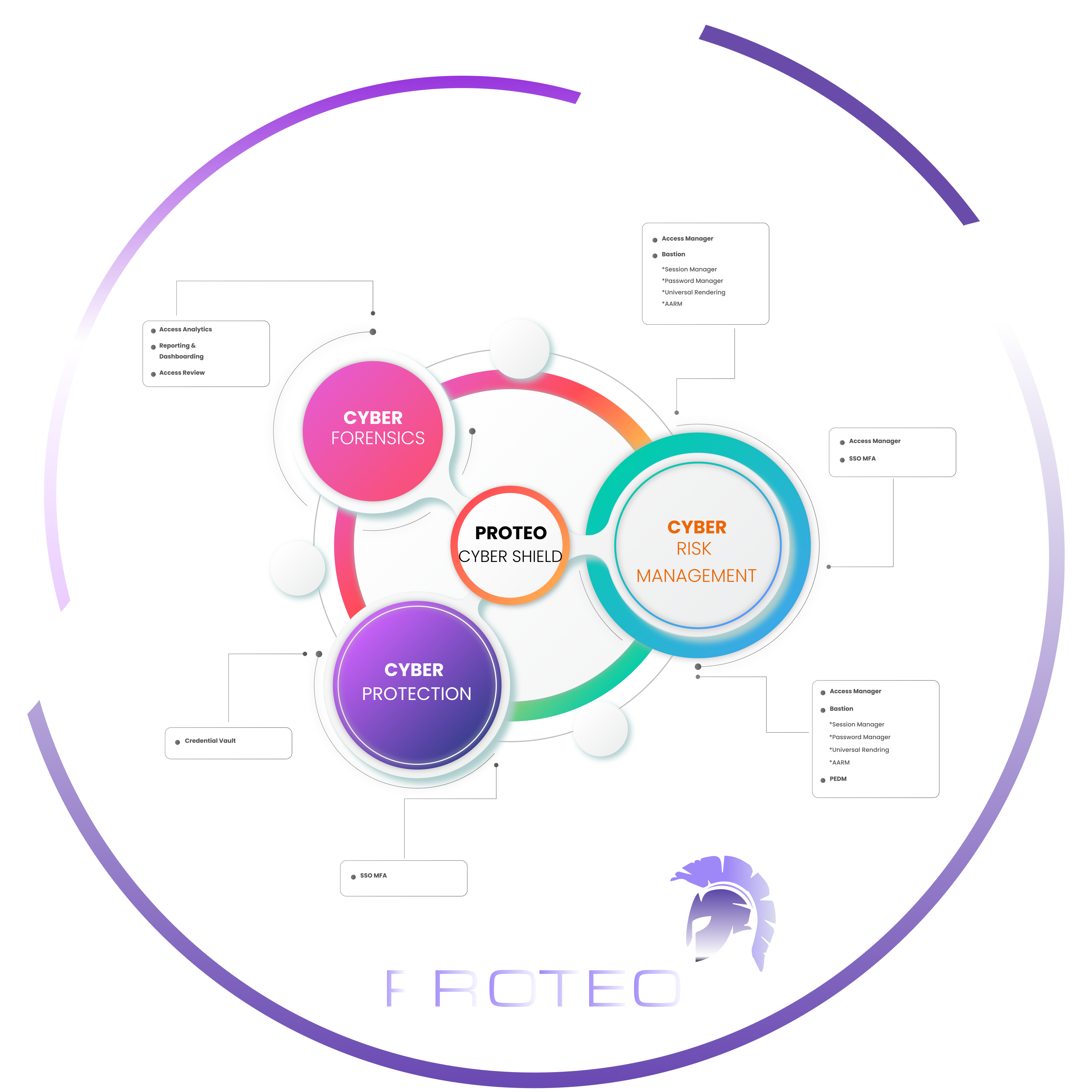
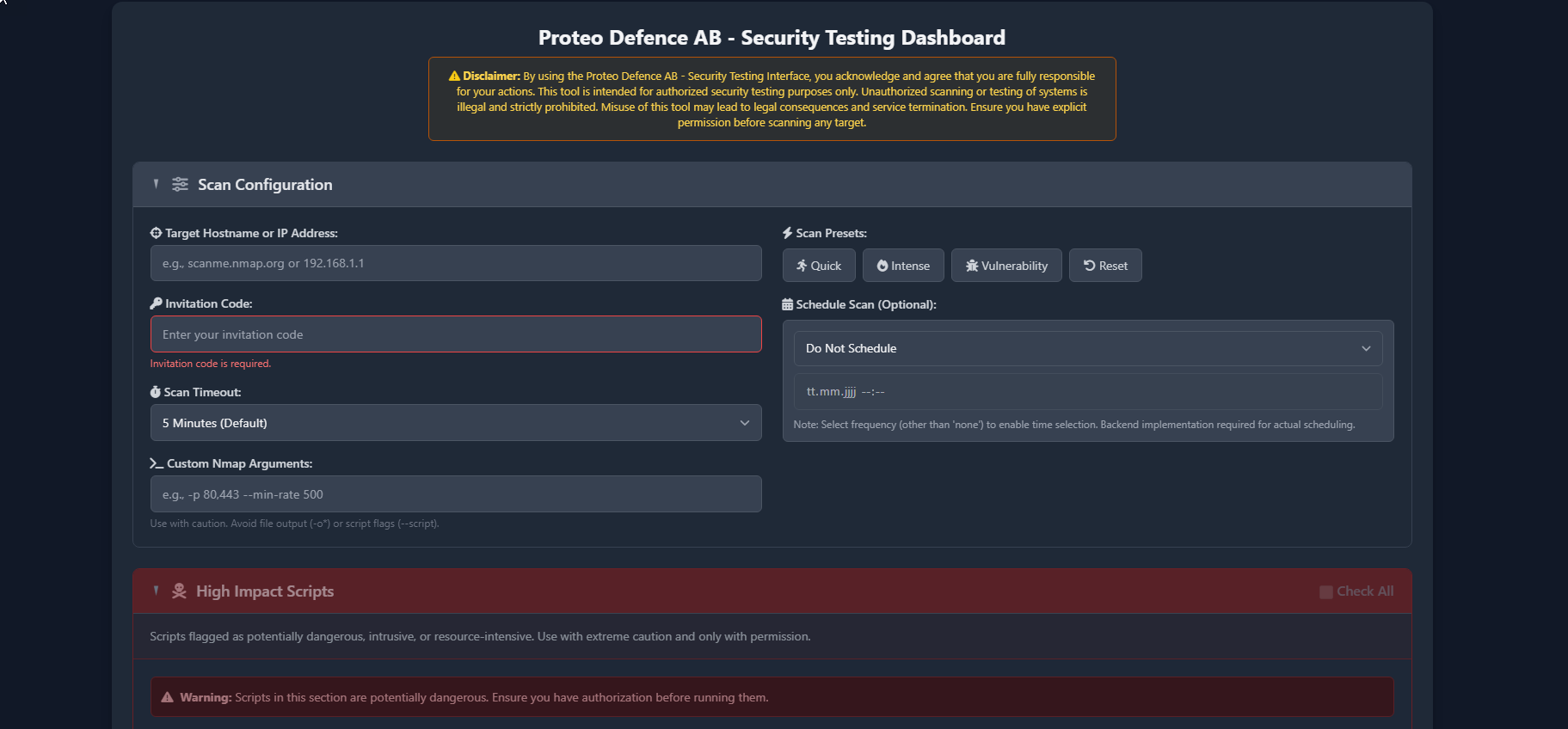
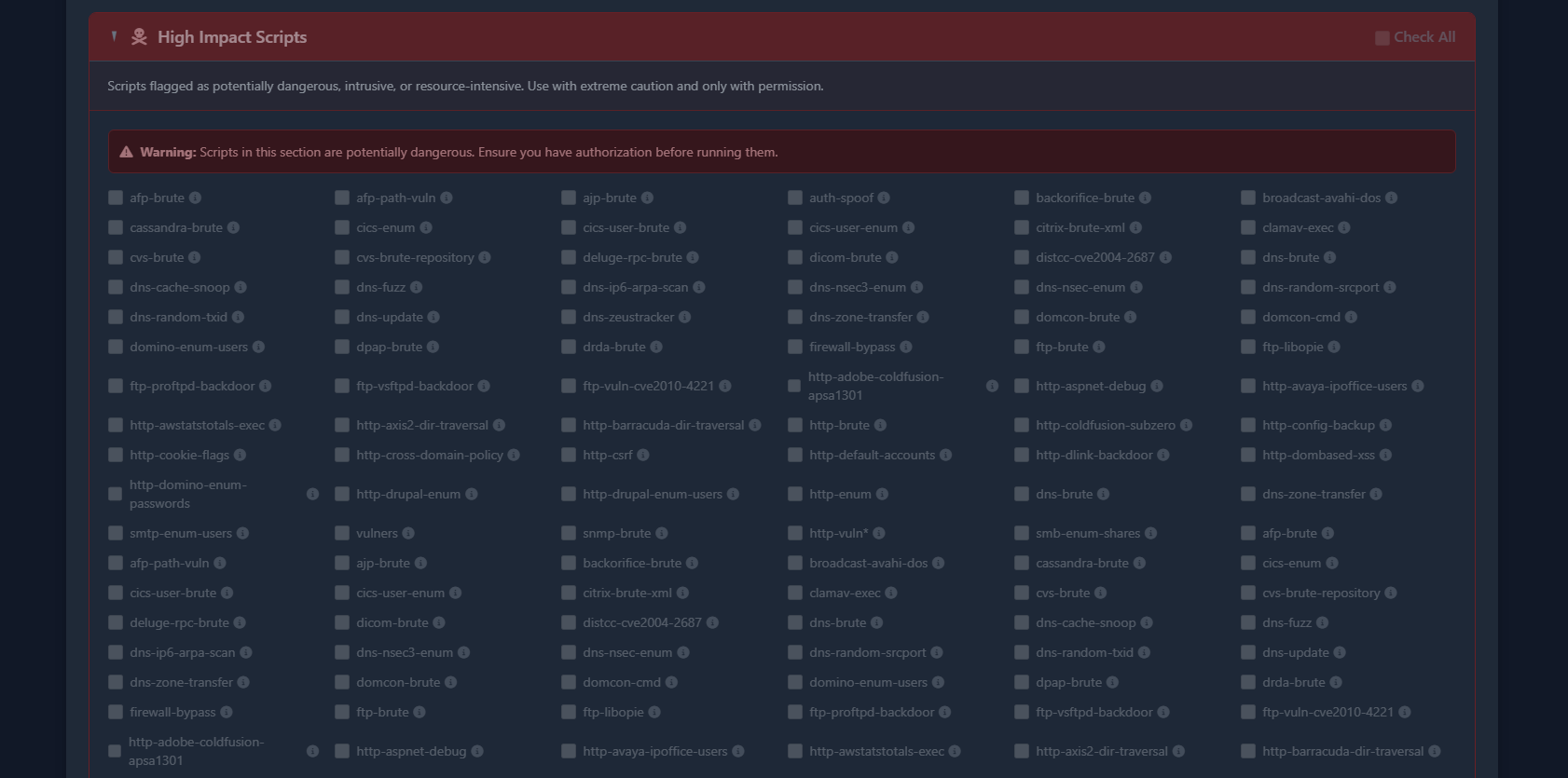
Project
Full CyberResilience Audit
As part of a comprehensive cyber security audit, we supported a pan-European online broker in the further development of its IT security architecture in the context of the new DORA regulation (Digital Operational Resilience Act). The starting point was the question of the extent to which existing structures already meet the increasing requirements for operational resilience, attack detection and regulatory verifiability.
Together with the relevant specialist and IT units, the status quo of the technical and organizational security measures was systematically analysed. Identified weaknesses were prioritized based on risk and translated into a catalog of measures that could be implemented and seamlessly integrated into existing processes. A particular focus was placed on hardening critical systems and establishing a consistent governance and control framework to anchor the DORA requirements in the long term.
-
DORA gap analysis and implementation concept
-
Testing and hardening the IT architecture
-
Establishment of dynamic cyber risk management
-
Integration of audit findings into the existing ISMS
Project
CyberCrime Forensics
After a targeted cyberattack on a trading platform for digital currencies, large quantities of cryptocurrencies were stolen from customer wallets. Our task was to forensically analyze the attack patterns, identify the technical vulnerabilities and provide a comprehensible account of how the attacker had moved through the system landscape.
In addition to investigating the crime, the focus was on developing an action plan to eliminate the security vulnerabilities and sustainably increase cyber resilience. In close coordination with IT, compliance and management, a future-proof security concept was established that includes both technical protection mechanisms and organizational emergency processes.
-
Forensic investigation of the attack vector
-
Weak point analysis and technical root cause analysis
-
Development of a multi-level security concept
-
Introduction of an early warning system for wallet-related anomalies
Project
Forensic task force deployment after token theft from a crypto wallet
We were called in as part of a task force operation initiated by the authorities following the outflow of digital assets from a crypto wallet. The aim of the project was to reconstruct the technical and organizational path of the incident in a comprehensible manner and to gain reliable insights into the cause of the token loss. Due to the ongoing investigations, the highest level of confidentiality was maintained throughout the entire project.
The investigation focused on the forensic analysis of the underlying system landscape, access paths and relevant log and transaction data. The analysis was open-ended and without any prior assumptions regarding a technical exploit. In the course of the investigations, there was growing evidence that access was not through a vulnerability in the wallet or blockchain infrastructure itself, but through targeted social engineering measures that led to access and administration rights being compromised. The results of the investigation were processed in a structured manner and handed over to the relevant investigating authorities for further use.
-
Forensic analysis of a token outflow from a crypto wallet
-
Reconstruction of access and transaction paths
-
Evaluation of system, access and event logs
-
Identification of social engineering-based attack patterns
Project
Technical code forensics as part of an M&A transaction with a high technology content
As part of a complex M&A project with a strong focus on technology and software, we were called in by a leading commercial law firm to independently assess the technical substance of the target company. For external parties, the underlying software platform represented a largely closed black box whose quality, integrity and legal harmlessness could only be assessed to a limited extent on the basis of traditional due diligence approaches.
The task was to carry out targeted forensic investigations at code and architecture level to determine whether the software was free of copyright risks, did not contain any security-critical gateways for malware and generally corresponded to a contemporary, resilient understanding of architecture. The analysis was independent and open-ended. Significant deficits were identified in two of the three dimensions examined, which ruled out an immediate transaction release. The project could only be brought to a successful conclusion once the identified deficiencies had been fully rectified and a new technical validation had been carried out.
-
Forensic code and architecture review in the M&A context
-
Analysis of possible copyright and license infringements
-
Identification of security-critical vulnerabilities at code level
-
Evaluation of the software architecture with regard to scalability and maintainability
Project
Integrated security & trust management platform for automated compliance management
The starting point for the development of our own security and trust management platform was the increasing complexity of regulatory requirements and the realization that traditional compliance approaches no longer meet the dynamic requirements of modern IT and business models. The aim was to create a central platform that does not document security, governance and compliance requirements in isolation, but manages them holistically, continuously and automatically.
The platform developed automates the requirements of a large number of internationally recognized security and compliance frameworks. It consolidates technical, organizational and procedural evidence, evaluates the current maturity level in real time and makes deviations and the need for action transparent. The high degree of automation drastically reduces manual effort, significantly accelerates audit processes and establishes compliance as a continuous, controllable state. The platform has been developed entirely in-house, has a modular structure and is designed for use in highly regulated environments.
-
Automation of international security and compliance frameworks
-
Continuous determination and updating of the safety and compliance maturity level
-
Central consolidation of technical, organizational and procedural evidence
-
Real-time transparency on deviations, risks and measures
Project
Cyber due diligence & cyber risk analysis in preparation for external IT audits
In the run-up to an announced external IT audit by a supervisory or control authority, a regulated company commissioned us to carry out a comprehensive cyber due diligence. The aim was to review existing structures, processes and security measures for their regulatory, organizational and technical adequacy at an early stage and to address identified weaknesses in a structured manner before the actual audit.
As part of the project, both the existing IT and security landscape as well as relevant business and control processes were analyzed holistically. In addition to evaluating technical protective measures, a particular focus was placed on the formal design of procedures, role models and authorization systems. The results were transferred into a consistent cyber risk assessment and served as the basis for deriving an integrated cyber security, data security and DORA strategy that ensures both operational feasibility and regulatory verifiability.
-
Carrying out cyber due diligence as a preparatory measure for the audit
-
Inventory and process analyses along IT, security and governance lines
-
Documentation of procedures, roles, responsibilities and control mechanisms
-
Analysis of authorization concepts and incompatibilities
Project
Incident, reporting and governance structures for a regulated financial services provider
The starting point for this project was the increasing public and regulatory attention to inadequately structured incident processes and delayed or inconsistent reporting of security-related incidents. A financial services provider operating throughout Europe approached us with the request to review existing incident and reporting procedures in their entirety and to align them in such a way that both the operational ability to act and regulatory verifiability are guaranteed at all times.
During the course of the project, the existing processes for detecting, classifying, escalating and reporting security incidents were analyzed along the entire life cycle. Particular attention was paid to the clear delineation of responsibilities, the decision-making logic for reportable incidents and the dovetailing of technical events with organizational and legal assessment steps. Together with IT, GRC, Legal and Management, a consistent governance framework was developed that comprehensibly links operational processes, regulatory requirements and management decisions.
-
Analysis and restructuring of the incident lifecycle processes
-
Definition of clear roles, responsibilities and escalation levels
-
Development of a consistent reporting and classification logic
-
Mapping of regulatory requirements in operational decision-making processes
Project
API & platform security for a data-driven financial and service platform
Against the backdrop of publicly known data leaks and cases of misuse via inadequately secured programming interfaces, the operator of a digital platform used throughout Europe turned to us to fundamentally review the security of its API-based system landscape. The aim was to establish the growing dependence on APIs not as a risk factor, but as a controllable component of the overall architecture.
As part of the project, all productive and internal interfaces were systematically recorded and analyzed along typical attack scenarios. The focus was less on classic vulnerabilities and more on logical access paths, authorization models and opportunities for misuse within complex platform processes. Together with development, operations and architecture, identified risks were prioritized and transferred into a consistent security and governance concept that could be integrated into existing development and operational processes.
-
Complete recording and classification of all APIs
-
Analysis of authentication, authorization and token mechanisms
-
Checking the API logic for misuse and escalation scenarios
-
Implementation of an end-to-end API governance and control framework
Project
Ransomware resilience & incident readiness for a KRITIS-related infrastructure company
Following several publicly known ransomware incidents in critical infrastructures, a nationwide infrastructure company approached us with the aim of reviewing and strengthening its own resilience to targeted cyberattacks in a structured manner. The focus was not just on prevention, but in particular on the ability to detect security incidents at an early stage, limit them effectively and handle them correctly in accordance with regulations.
As part of the project, the existing IT and security architecture was analyzed holistically - from network segmentation and access and authorization concepts to backup and restart procedures. Together with IT, operations and management, realistic attack scenarios were derived, existing protection mechanisms evaluated and a prioritized catalog of measures developed. A particular focus was placed on dovetailing technical protection measures with clearly defined decision-making, escalation and communication channels in the event of an emergency.
-
Ransomware readiness assessment based on real attack scenarios
-
Analysis and hardening of critical system and network segments
-
Evaluation and realignment of backup and recovery strategies
-
Conception of a structured incident response framework
Project
Preventive social engineering & awareness program for a knowledge-intensive organization
After several publicly known incidents in which attacks were not carried out via technical vulnerabilities but through targeted manipulation of employees, a knowledge-intensive organization decided to take a preventive approach. The aim was not to treat social engineering as an isolated training topic, but to systematically integrate it into the security architecture, processes and corporate culture as a real cyber risk.
As part of the project, typical attack vectors were analysed, real attack scenarios were modelled and organization-specific risk profiles were created. Based on this, a multi-stage awareness and prevention concept was developed that links technical, organizational and human factors. Particular attention was paid to sustainably anchoring security awareness not through one-off training sessions, but through continuous sensitization, measurable learning progress and clear escalation mechanisms.
-
Analysis of organization-specific social engineering risk profiles
-
Development of realistic attack scenarios (phishing, pretexting, impersonation)
-
Implementation of targeted awareness and simulation training
-
Definition of clear reporting and escalation channels for suspected cases
Project
Secure Phone - self-sufficient, tap-proof communication solution for highly sensitive applications
The starting point for the development of the Secure Phone was a mandate from a particularly sensitive area of the economy, where the protection of strategic company assets had top priority. The aim was not only to detect unwanted information leaks reactively, but also to prevent them proactively - especially in scenarios in which targeted infiltration, technical surveillance or eavesdropping could not be ruled out.
Based on these requirements, a completely independent communication solution was designed that meets the highest security requirements at both hardware and software level. The hardware developed is completely self-sufficient, does not rely on external dependencies and was designed in such a way that potential points of attack and interception are systematically excluded. In addition, a specially adapted system architecture was implemented to enable secure communication even in particularly exposed environments.
-
Development of completely self-sufficient, tap-proof communication hardware
-
Protection against targeted eavesdropping, infiltration and manipulation attempts
-
Reduction of external dependencies at hardware and system level
-
Specially hardened communication and operating system architecture
Project
CyberRisk dashboard with real-time assessment and management focus
The starting point for the development of the CyberRisk dashboard was the recurring observation that, although cyber risks are recorded in technical detail, their significance for management decisions is often fragmented or delayed. The aim was therefore to create a central platform that consolidates and contextualizes security-relevant information from different sources and transfers it into an ongoing, comprehensible risk assessment.
The dashboard was designed as a modular in-house development that links technical events, organizational factors and regulatory requirements. Relevant signals are aggregated, prioritized and evaluated along defined risk categories in real time. Particular emphasis was placed on clearly separating technical detail and management suitability: While operational units can perform in-depth analyses, decision-makers receive a condensed, reliable view of the current cyber risk situation and its development over time.
-
Central aggregation of technical, organizational and regulatory risk signals
-
Real-time-based assessment and prioritization of cyber risks
-
Separation of operational detail views and management dashboards
-
Mapping of risk trends, escalation levels and action status
Project
Automated DORA readiness logic for continuous resilience assessment
The starting point for the development of the automated DORA readiness logic was the realization that regulatory requirements for digital operational resilience are often assessed selectively, while their actual degree of fulfillment is only visible to a limited extent during ongoing operations. The aim was therefore to develop a logic that does not statically document the DORA maturity level, but rather continuously, comprehensibly and auditably maps it.
The solution developed translates the requirements of the DORA regulation into structured test criteria, control parameters and measurable indicators. Technical, organizational and procedural information is automatically merged, evaluated and transferred to a consistent maturity level. Deviations, need for action and progress are presented transparently and can be tracked both operationally and at management level. The logic has a modular structure and can be integrated into existing governance, risk and control systems.
-
Translation of regulatory DORA requirements into auditable control criteria
-
Automated determination and updating of the DORA maturity level
-
Linking technical, organizational and process-related information
-
Transparent presentation of deviations, measures and progress
Project
Audit trail and evidence repository for audit-proof evidence management
The starting point for the development of the audit trail and evidence repository was the recurring experience that, although safety-relevant evidence is available in terms of content, it is distributed across different systems, responsibilities and formats. This not only makes internal control more difficult, but in particular the structured preparation and implementation of external audits.
The developed solution serves as a central, audit-proof repository for all audit-relevant information in the context of cybersecurity, IT governance and regulatory requirements. Events, measures, decisions and technical evidence are automatically or manually recorded, versioned and placed in a traceable chronological context. The complete audit trail enables both operational developments and management decisions to be documented consistently and reliably.
-
Centralized, structured filing of examination-relevant evidence
-
Seamless documentation of measures, decisions and events
-
Versioning and chronological traceability of all artifacts
-
Supporting internal and external audits with consistent evidence
Project
Automated security assessment tool for widely used CMS platforms with certification approach
The starting point for the development of this tool was the observation that a large number of publicly accessible web systems are based on widespread content management systems and are often inadequately maintained or secured. These systems represent an attractive target for automated attacks and often serve as a gateway for further compromises. The aim was to create a scalable test procedure that recognizes security risks at an early stage and provides administrators with concrete support in remedying them.
The developed solution automatically analyzes CMS installations for known and context-related security problems. In addition to identifying technical vulnerabilities, concrete, actionable recommendations are provided based on the respective system configuration. In combination with a downstream, structured security audit, the security status of the system can then be validated and documented in the form of a certification. This turns a purely technical test into a comprehensible, auditable proof of security.
-
Automated security analysis of widely used CMS systems
-
Identification of technical weaknesses and misconfigurations
-
Derivation of concrete, administratively implementable recommendations for action
-
Scalable use even in large system landscapes
Project
Forensic elimination of a hardware lock as part of an official investigation
In the course of ongoing investigations, we were called in by the authorities to support the technical analysis and removal of a hardware-based access protection. The affected device type was secured by a proprietary hardware lock that prevented access to stored data and further technical analysis. The aim of the operation was to remove the locking mechanism in a controlled manner without compromising the integrity of potentially evidence-relevant information.
The investigation was carried out under strictly controlled conditions and in close coordination with the relevant authorities. The focus was on analyzing the underlying hardware architecture, identifying the locking mechanism and developing a targeted procedure to circumvent the lock. Access was established exclusively for forensic purposes, all steps were documented and the results were made available in a usable form.
-
Forensic analysis of hardware-based access locks
-
Investigation of proprietary lock and protection mechanisms
-
Controlled removal of hardware locks with preservation of evidence
-
In-depth analysis of hardware architecture and memory accesses
Project
Red teaming deployment for realistic testing of cyber resilience
As part of a strategic security programme, a major company commissioned us to carry out a red teaming exercise to test the actual resilience of its technical and organizational security measures under realistic attack conditions. The aim was not to identify individual vulnerabilities in isolation, but to test the interplay between technology, processes and human behavior as a whole.
The test was carried out on the basis of defined target images and clear framework conditions. Using realistic attack vectors, attempts were made to gain unauthorized access, bypass security mechanisms and compromise critical systems. Both technical and social attack methods were used. The results were not simply documented as a list of findings, but were translated into concrete risk scenarios and prioritized measures together with the responsible departments.
-
Planning and implementation of a controlled red teaming operation
-
Simulation of real attack and escalation paths
-
Combination of technical attacks and social engineering methods
-
Assessment of the ability to recognize, react and escalate
Project
C-Level Red Teaming to check decision-making and crisis capability
As part of a company-wide security program, C-level red teaming was initiated to review the decision-making, escalation and control capabilities at the highest management level under realistic attack conditions, rather than primarily technical protective measures. The starting point was the realization that cyber incidents fail less because of a lack of technology than because of unclear responsibilities, delayed decisions or contradictory communication at management level.
The red teaming exercise combined realistic technical attack scenarios with targeted stress and decision-making situations for top management. Security-relevant events were escalated step by step, decision options were deliberately shortened and external framework conditions were simulated. The aim was to gain transparency about how effectively management bodies act under time pressure, evaluate information, assume responsibility and take control. The results were evaluated in a structured manner and translated into specific governance, role and process adjustments.
-
Conception and implementation of a C-level-focused red teaming scenario
-
Simulation of critical decision-making and escalation situations
-
Evaluation of understanding of roles, responsibilities and decision-making logic
-
Analysis of communication and coordination processes in the event of a crisis
Project
Targeted countermeasures and tracing in the event of ongoing data outflow
In a commercially active company, we were called in on the initiative of the information security officer after unusual system activity was detected. Initial analyses indicated an advanced compromise of several servers, which had already resulted in unauthorized data outflows. The aim of the operation was to determine the scope of the attack, control the outflow and gain reliable information about the attackers.
During the course of the investigation, a conscious decision was made not to immediately shut down the affected systems. Instead, controlled countermeasures were introduced to make the attackers believe that they still had access to supposedly sensitive information. Targeted technical artifacts and proprietary technologies were used to track activities, analyze communication paths and enable tracing. The knowledge gained ultimately led to the identification of the attackers and was handed over to the responsible authorities in a usable form.
-
Forensic analysis of compromised servers and ongoing data outflows
-
Controlled continuation of the attack to gain reliable findings
-
Use of targeted deception and countermeasures
-
Use of proprietary technologies for technical traceability
Project
Analysis and clarification of an Advanced Persistent Threat (APT)
In the course of recurring, initially inconspicuous security incidents, we were commissioned to investigate the possibility of a long-term, targeted attack. Individual indicators suggested that this was not an opportunistic attack, but a systematic, covert compromise with a clearly defined target.
The analysis focused on reconstructing the temporal course of the attack, identifying persistent access points and correlating technical traces across multiple systems. Particular attention was paid to the separation of legitimate and manipulated activities as well as the identification of cloaking mechanisms that had prevented early detection. The knowledge gained enabled a reliable classification of the nature of the attack, the targeted interruption of persistence and the derivation of sustainable protection and hardening measures.
-
Analysis of long-term, targeted attack patterns (APT)
-
Reconstruction of attack phases and persistence mechanisms
-
Correlation of distributed technical indicators over longer periods of time
-
Identification of hidden access and control structures
Project
Data protection forensics and darknet analysis to clarify internal data leaks
An e-commerce provider approached us after several customers had contacted us and expressed the suspicion that personal address data had been unlawfully passed on or sold. In addition to the acute concern about possible data protection breaches, there was also the risk of considerable reputational damage. The aim of the project was to examine the allegations objectively, create transparency and actively contribute to clarification.
As part of the project, the existing data protection and access concept was first reviewed, including the technical and organizational measures to protect personal data. At the same time, a targeted analysis of relevant darknet marketplaces and communication channels was carried out in order to identify possible indications of a data leak. The investigation revealed that the threat did not come from outside, but from within the organization: an employee had illegally gained access to databases and exfiltrated personal data. The findings were documented in a structured manner and made available for further processing.
-
Review of the data protection and access concept
-
Analysis of internal authorization and control mechanisms
-
Targeted darknet search for evidence of data leaks
-
Forensic reconstruction of internal access and exfiltration paths